It is a “dark forest” for the average user. If you are not sure that this is where the problem with your computer lies, then it is better not to touch anything there at all and leave it to professionals to deal with the problems. Today we will talk about what threats one small and inconspicuous text file. What should it look like? How to distinguish it from a virus?
Definition
First, let's figure out what kind of beast this is - Hosts? This is a file responsible for blocking Internet pages and redirecting IP addresses. If you enter the web address of any Internet resource into it, then the computer user will not be able to access the blocked site or will be redirected to another link specified in the file.
In fact, this file is used by most system administrators to disable social media for employees, as well as for organizing and blocking sites inappropriate for children. So if you cannot access any resource from your work computer, be sure to first check the contents of the file, which we will talk about a little later. Because it looks right
The main thing that determines the authenticity of a file and its belonging to the system and not to viruses is its contents. Or rather, the text written in it. What should the Hosts file look like in Windows 7 and other operating systems from the inside?
To open the file we are studying, use Notepad. You will see English-language instructions for using this tool. It consists of 20 lines starting with the "#" character. Here's some sample content:
- The first line contains the rights to the OS. 1993-... - the year of Microsoft's existence. The second number will be the release date of your OS version. You can check the authenticity of the file by right-clicking on “My Computer - Properties”. There you can find the OS version and release date. They must match the file.
- Then there are 10 lines explaining what you need this file.
- And finally, examples of how to register a block.

Location
The location of the file also plays an important role. How will the file we are looking at perform its function if it is not in the right folder?
So, what should it look like and where should it be located. Depending on the OS version, it may be located in different folders, but it will always be the original Windows system:
- For Win98 and ME, the “Hosts” file is located in the root of C:\WINDOWS.
- In WinXP and later versions, Hosts is located in the following directory: C:\WINDOWS\SYSTEM32\DRIVERS\ETC. This is where the working version of the file is located if you have a system or it initially contains several switchable versions and patches. Then you may find a second, similar copy of the file, but it will also be in the system folder.
Size
What does the correct Hosts file look like? Its size is also initially determined. If you opened and saw only what was described in the previous paragraph, then the file size will be 824 bytes. Or it will be empty if the instruction was removed from there.

Any deviation suggests that something other than comments was written into the file. On the one hand, these can be sites listed there by system administrators. On the other hand, if we are talking about a home computer and you are absolutely sure that no one has messed with it, you should think about whether this file is a virus.
The main thing is to remember that no antivirus works with the Hosts file. More precisely, security programs block the ability of programs from an unknown manufacturer to change the file. Thus, no one can enter any information there without your knowledge, block access to your favorite sites, or, worse, redirect to a copy of the portal you need, where you can inadvertently enter your personal data, which will later go to attackers. But if this happens, then immediately check your computer for viruses.
Virus
Now you know what the Hosts file should look like. It’s also worth figuring out what it shouldn’t look like.
- This file is not hidden, that is, by going to system folder, in which it is located, you can always see it. If he tries to disguise himself, this is at least a sign of viral activity.
- If you find it in any folder other than the one indicated above, delete it, and it appears again, this should also alert you.

Among other things, the registry can help with the question of what the Hosts file should look like. The fact is that the path to the file is written in a very specific directory, and in this way you can determine whether the file you found is true or false (a virus).
- To see the location of “Hosts” in the registry, run and type regedit.
- Path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Tcpip\Parameters
- By clicking on the settings folder, look to the right. In the list of parameters we are interested in DataBasePath. It is in it that the path to the true Hosts file is written. Any deviation from this path means that the file you found is malware.
That's all. We analyzed all the characteristic features and determined what the Hosts file should actually look like.
After entering the required site in the browser, suppose Google.com , the browser sequentially (according to priority) looks for a match between this domain name and the IP addressee (because it is IP addresses that network devices work with).
A) the specified site is checked in the hosts file, if it finds a match (let’s assume 1.1.1.1 Google.com is written in the hosts file), then the contents of IP - 1.1.1.1 will be opened for you, if there is no specified domain name, proceed to the next step;
b) the cache DNS is checked (if you have previously opened Google.com, then most likely the IP of this site is stored in the DNS cache of your computer/laptop), if the IP of the site is indicated there, then the page opens to you, if not, it proceeds to the last stage;
V) the request goes to the DNS server (it is registered manually in the network connection settings or issued via DHCP), if the DNS server does not have the specified site, it will “ask” another DNS server until it finds it (if, of course, it exists at all) and the site is successful will open.
The hosts file is located at C:\Windows\System32\Drivers\etc\hosts (if C- system disk). You can open it with a regular notepad. If you have not made changes to the hosts file, then the following will be written there:
|
Hosts file in Windows XP: 127.0.0.1 localhost |
Hosts file in Windows Vista: 127.0.0.1 localhost |
|
Hosts file in Windows 7: # 38.25.63.10 x.acme.com # x client host # localhost name resolution is handled within DNS itself. |
Hosts file in Windows 8 # Copyright (c) 1993-2009 Microsoft Corp. # localhost name resolution is handled within DNS itself. |
As you can see, regardless of the version, the host file is not very different, but if a virus “worked” on the hosts file, various sites and IPs can be added there. For example:
127.0.0.1 ftp.kasperskylab.ru
127.0.0.1 ids.kaspersky-labs.com
127.0.0.1 vk.com
127.0.0.1 drweb.com
Such additions to the file prevent you from accessing the specified sites.
1.2.3.4 ftp.kasperskylab.ru
1.2.3.4 ids.kaspersky-labs.com
1.2.3.4 vk.com
1.2.3.4 drweb.com
Such additions in the file when opening the specified sites will redirect you to other sites, possibly infected with viruses (IP-1.2.3.4- are fictitious).
If you find that the hosts file has been changed, it needs to be corrected. In Windows XP, the file is simply opened in Notepad, the necessary changes are made and saved (you must log in as an administrator). On other versions (Windows Vista, 7, 8), you must give permission to change the file. To do this, open the folder in which hosts is located C:\Windows\System32\Drivers\etc(if drive C is system). Right click on hosts and choose "Properties".
Select a tab "Safety", then select the user under which you work on your computer/laptop (in this example, this is a website) and press the button "Change". A window will open "Permissions for the group "hosts"", select the user again and assign full rights to the file, click "OK", in the window "Properties: hosts", Same "OK".

After that, open hosts with Notepad and return the file to original state, save the changes when finished.
Windows is far from Linux in terms of systematic use configuration files, in order to configure the functionality operating system. First of all, because Windows uses the registry for this.
But still, there are such files in Windows, and knowing their purpose is sometimes useful. An important repository of configuration options includes a file called Hosts. The file name does not have an extension, so when automatic search there is no need to specify it.
In the course of the presentation, we will focus on the seventh version of the OS, as the most widely used by consumers (Microsoft's tricks in the G8 failed to convince users that Metro is cool).
Essentially, we are dealing with a repository of domain names, similar to DNS server names. The benefit of using it is that the computer owner is able to regulate the priorities of domains when translating them into real network addresses when accessing Internet resources.
File domains take precedence over any external ones DNS addresses, even those specified in the settings network connections. The default storage location in 7 looks like this: %SystemRoot%\system32\drivers\etc\hosts. However, this path is not possible. The system administrator can override it by changing the registry key named HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Tcpip\Parameters\DataBasePath. Files with a similar name and purpose are included not only in the Windows system environment; they can be found in Unix-like OSes, Mac-OS and even on the Android platform.
Internal structure of Hosts records and storage manipulation
Although Hosts does not have an extension, it looks like a regular one from the inside test file with entries approximately in this format: 127.0.0.1 localhost. That is, with a structure consisting of a domain's IP address and its symbolic name, separated by spaces or a tab character.
The example given is a mandatory entry in any such file. It corresponds to the address and name of the user's machine itself. All other entries look similar to this one. With the help of the information placed here, a variety of problems can be solved. For example:
- You can associate the name localhost not with the address of the local machine, but with the address of any computer on the enterprise intranet. This is often done by system administrators of enterprises and organizations.
- Similar associations can be used to optimize access to external hosts. If you create a record with a range of IP addresses corresponding to the real addresses of the desired sites, then their pages will load faster than when accessing the provider’s DNS database.
- Another useful option is the ability to organize blocking of unwanted domains (for example, domains of advertising sites). To do this, all such domains are assigned a local machine address – 127.0.0.1

In principle, hosts is an outdated technology, supported for reasons of backward compatibility.
In addition, it has a serious drawback: if the network connection uses an intermediate proxy server, then all storage entries are simply ignored. There are also security concerns.
The fact is that many viruses like to dig into the contents of a file and change it at their discretion. One of the recommendations given in the event of a virus attack is to open the file in Notepad and delete from it all entries located below the localhost entry.
Recently I needed to fix the hosts file, and where to find the hosts file, I didn't know, so I had to comb for the answer I needed. Fortunately, there was a lot of information, but just in case, I still decided to leave the answer to my question on the pages of the Computer Malfunctions blog.
Where is the hosts file located in Windows XP?
Located HOST file in Windows XP by the address:
C:\WINDOWS\system32\drivers\etc\
Open hosts file You can use any text editor, for example, Windows Notepad.
What does the hosts file look like?
If your task is hosts file recovery, then you can copy the typical contents of the hosts file for Windows XP below. In fact, the contents of the hosts file can be limited to just one line "127.0.0.1 localhost". Everything else is just explanatory commentary. On Windows XP the hosts file looks like So:
# (C) Microsoft Corp., 1993-1999
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains mappings of IP addresses to hostnames.
# Each element must be on a separate line. The IP address must
# should be in the first column and must be followed by the appropriate name.
# The IP address and hostname must be separated by at least one space.
#
# Additionally, some lines may contain comments
# (such as this line), they must follow the node name and be separated
# from it with the symbol "#".
#
# For example:
#
# 102.54.94.97 rhino.acme.com # origin server
# 38.25.63.10 x.acme.com # client node x127.0.0.1 localhost
And finally, if your system is not Windows XP, then I recommend that you read the article on restoring the hosts file for Windows 7, Windows Vista, Windows Server 2008, Windows Server 2003 on the official Microsoft support website: http://support.microsoft.com/kb/972034/ru.
The hosts file is a rather vulnerable place in the Windows operating system. This file becomes the number one target for almost all viruses and Trojans that manage to infect a computer.
The purpose of this file is to store a list of domains and their corresponding IP addresses. The operating system uses this list to convert domains to IP addresses and vice versa.
Every time you enter the address of the site you need into the address bar of your browser, a request is made to convert the domain to an IP address. Currently, this translation is performed by a service called DNS. But, at the dawn of the development of the Internet, the hosts file was the only way to associate a symbolic name (domain) with a specific IP address.
Even now, this file has a direct impact on the transformation of symbolic names. If you add an entry to the hosts file that will associate the IP address with the domain, then such an entry will work perfectly. This is exactly what developers of viruses, Trojans and other malicious programs use.
As for the file structure, the hosts file is a regular text file without an extension. That is, this file is not called hosts.txt, but simply hosts. To edit it, you can use the regular text editor Notepad.

The standard hosts file consists of several lines that begin with the “#” character. Such lines are not taken into account by the operating system and are simply comments.
Also in the standard hosts file there is an entry “127.0.0.1 localhost”. This entry means that when you access the localhost symbolic name, you will be accessing your own computer.
Fraud with the hosts file
There are two classic way benefit from making changes to the hosts file. Firstly, it can be used to block access to sites and servers of antivirus programs.
For example, having infected a computer, the virus addsin the hosts file the following entry: “127.0.0.1 kaspersky.com”. When you try to open the kaspersky.com website, the operating system will connect to the IP address 127.0.0.1. Naturally, this is an incorrect IP address. This leads to Access to this site is completely blocked.As a result, the user of the infected computer cannot download antivirus or antivirus database updates.
In addition, virus developers can use another technique. By adding entries to the hosts file, they can redirect users to a fake site.
For example, having infected a computer, the virus adds the following entry to the hosts file: “90.80.70.60 vkontakte.ru.” Where “90.80.70.60” is the IP address of the attacker’s server. As a result, when trying to access a well-known site, the user ends up on a site that looks exactly the same, but is located on someone else’s server. As a result of such actions, fraudsters can obtain logins, passwords and other personal information of the user.
So, in case of any suspicion of virus infection or site substitution, the first thing you need to do is check the HOSTS file.
The malware disguises modification of the hosts file as follows:
To make it difficult to detect lines added by a virus, they are written to the end of the file
After a large empty area formed as a result of repeated line feeds;
After this, the original hosts file is assigned the Hidden attribute (by default hidden files and the folders are not visible);
A false hosts file is created, which, unlike the real hosts file (which has no extension), has the extension .txt (by default, extensions are not displayed for registered file types):

Where is the hosts file located?
Depending on the operating system version Windows file hosts can be located in different folders. For example, if you use Windows XP, Windows Vista, Windows 7 or Windows 8, then the file is located in the folderWINDOWS\system32\drivers\etc\

In the Windows NT and Windows 2000 operating systems, this file is located in the folder WINNT\system32\drivers\etc\
Editing the hosts file
You can edit the file hosts and in Notepad, delete unnecessary lines, or add your own.
In order to edit the hosts file, you need to launch Notepad in Administrator mode, and then open the file C:\Windows\System32\drivers\etc\hosts in it.
How to clean the hosts file
So, point by point.
Click "Start".

Choose "All programs".
Then select the item "Standard".
On "Notepad" click right click the mouse and select the item "Run as administrator."
In the notepad window that opens, select the File menu, then "Open..."
In the window that opens, select “Computer” on the left side of the window. 
Then open the disk WITH:.
Windows directory. 
System32 directory. 
Drivers directory. 
Catalog etc. 
When you open the etc directory, you will see an empty directory. In the lower right corner of the window, select "All files".
Select the hosts file and click the button "Open".
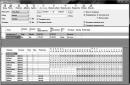
Check for the necessary content: at the beginning there are explanatory comments from Microsoft about what this file is and how to use it. Then there are several examples of how to enter various commands. All this is just plain text and does not carry any functions! We skip it and reach the end. Next should come the teams themselves. Unlike comments (i.e. plain text), they must begin not from the "#" sign, and from specific numbers, indicating the IP address.
Any commands in your hosts file after the following lines can be malicious:
- On Windows XP: 127.0.0.1 localhost
- On Windows Vista: ::1 localhost
- On Windows 7/8: # ::1 localhost
As you can see, host files are slightly different in different operating systems.
In order not to clean up anything unnecessary, you need to know how the commands are deciphered. There is nothing complicated here. At the beginning of each command there is digital ip address, then (separated by a space) the letter associated with it Domain name , and after it there may be a small a comment after the "#" sign.
Remember!
All commands starting from numbers 127.0.0.1(with the exception of, 127.0.0.1 localhos t) block access to various sites and Internet services. Which ones exactly, look in the next column following these numbers.
Teams having at the beginning any other numbers ip addresses, redirect(redirect) to fraudulent sites instead of official ones. Which sites have been replaced with fraudulent ones, also look in each column following these numbers.
Thus, it will not be difficult to guess which commands in your hosts file are malicious! If something is still not clear, look at the screenshot below.

Please keep this point in mind. Many virus commands can be hidden far at the very bottom of the file by cunning Internet attackers, so take the time to scroll the slider all the way down!

After you do the cleanup, don't forget to save all changes ( "File" --> "Save"). If you opened the hosts file from the Notepad program itself, when saving changes, in the column "File type" be sure to select an option "All files", otherwise notepad, instead of saving in the hosts file, will only make it text copy of hosts.txt, which is not system file and does not perform any functions!

After a successful save, do not forget to restart your computer.
How to block sites in hosts
So, the hosts file is already open and you see that it is built in the form of a regular text document.
At the beginning you will see comments (plain text that does not provide any functionality) starting with the symbol "#" . They may be followed by some functional commands prescribed by the system.
But we don't need them. We skip them and get to the very end of the document. Let's make a retreat. And now, here, we can already write the commands we need!

When finished working with the file, open the File menu, select "Save".
To understand how to correctly enter commands for blocking web resources, you need to know that each PC has its own so-called. loopback address, which sends any request back to itself. For any computers running Windows systems, Linux or Mac this address is always the same - 127.0.0.1 . Now, with the help of just this IP address, you can block any request to an unwanted site so that it is sent not to the requested resource, but to brotherly to the local computer.
This command in hosts is written as follows: " 127.0.0.1 domain name to block "Here are real examples: 127.0.0.1 mega-porno.ru, 127.0.0.1 odnoklassniki.ru, 127.0.0.1 vk.com etc.

That's all. Now access to all unwanted sites is securely blocked. The main thing is to resave the hosts file after making changes! Detailed instructions see above.
Restoring the hosts file after a virus infection
As already mentioned, today a large number of malware use the file hosts to block access to websites of popular portals or social networks. Often, instead of blocking sites malware redirect the user to pages that look similar to popular resources (social networks, email services, etc.), where an inattentive user enters credentials, which thus get to the attackers.
If the file contains entries like 127.0.0.1 odnoklassniki.ru 127.0.0.1 vkontakte.ru or the addresses of your sites that you cannot access, then first check your computer for “malware”, and then restore the file hosts
Many users who have been hacked are interested in where they can download the hosts file. However, search and download original hosts the file is not needed at all. You can fix it yourself, to do this you need to open text editor and delete everything except the line except “127.0.0.1 localhost”. This will allow you to unblock access to all sites and update your antivirus.
Let's take a closer look at the process of restoring the hosts file:
1. Open the folder in which this file is located. In order not to wander through directories for a long time in search of the desired folder, you can use a little trick. Press the key combination Windows+R to open the menu "Run". In the window that opens, enter the command "%systemroot%\system32\drivers\etc"and click OK.
2. After this, a folder will open in front of you in which the hosts file is located.
3. Next you need to do backup copy current file. In case something goes wrong. If the hosts file exists, then simply rename it to hosts.old. If the hosts file is not in this folder at all, then you can skip this item.
4.Create a new empty hosts file. To do this, right-click in the etc folder and select"Create Text Document»
5. When the file is created, it must be renamed to hosts. When renaming, a window will appear with a warning that the file will be saved without an extension. Close the warning window by clicking OK.
6. Once the new hosts file has been created, it can be edited. To do this, open the file using Notepad.
7. Depending on the version of the operating system, the contents of the standard hosts file may differ.
This is what all, without exception, “clean” hosts files should look like. 


Note!
- For Windows XP and Windows Server 2003 you need to add "127.0.0.1 localhost"
- Windows Vista, Windows Server 2008, Windows 7 and Windows 8 you need to add two lines: "127.0.0.1 localhost" and "::1 localhost"
If you ever find missing or, conversely, unnecessary entries in such a file, it is better to delete them quickly. Especially if they were not made by you or without your consent. Most likely, this is the result of viruses!
Restoring the default hosts file in Windows 7: Copy the text below into a file.
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
#space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a "#" symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host # localhost name resolution is handled within DNS itself.
#127.0.0.1 localhost
# ::1 localhost
Save and close the file.