By default, all infected files will be moved to the "INFECTED.!!!" folder. DrWeb program, however, these settings can also be specified in the launch line using the /CU[P] parameter - where you can choose: R - (rename) rename (by default, the first character in the file name changes to "#"), D - ( delete) delete, M - (move) move (default to folder "INFECTED.!!!"). Parameter P - indicates whether it is necessary to ask the user for permission to perform an action (disabled by default).
Acronis True Image disk archiver launch options.
System administrators, and many users of home computers are familiar with the family of programs for creating disk images (Images) from Acronis. There are versions for both regular PCs running Windows and server platforms. The convenience of the program is that during image creation, data integrity is ensured at the level disk devices even if programs are being executed from the disk being archived. This means that data that is changed while the program is running will not be saved in the image, but previous state will remain. WinRar archiver, for example, when trying to archive a program running in this moment, will report an error. In addition, Acronis True Image series products allow you to create disaster recovery disks, view the contents of an image, etc...
If you have to constantly create an image of the same disk (usually the disk where the OS is located), you can also create a command on the command line, for example:
C:\Programms\TrueImageCmd.exe /create /partition:1-1 /filename:F:\backup.tib
Here, attention should be paid to the fact that command line not the executable file of the program is launched, but special utility TrueImageCmd.exe included in the installation package of the program. In this line:
C:\Programms\TrueImageCmd.exe is the path to the TrueImageCmd.exe file.
/partition:1-1 - number of the disk and partition on the disk from which you want to create an image
/filename:F:\backup.tib is the path to the image file that will be created by the program.
Thus, creating a disk image can be done with just one command from the command line, without going through the path of entering settings each time, which is inevitable when using the window interface of the True Image program. Also, at startup, you can set additional parameters, such as the degree of compression of the archive image, the password for opening the image, etc. All of them are described in more detail in the program help.
3. Launching the WinRar archiver.
The well-known WinRar archiver, unlike the Acronis True Image program, is convenient to use to create archival copies individual files and folders, not entire drives. If you need to periodically create copies of the same files and / or folders, you can also use the launch mode from the command line.
Command line example for running an archiving task:
"C:\Program Files\WinRAR\WinRAR.exe" u -r -y -ep1 c:\archive\arch.rar "c:\MyFiles\"
C:\Program Files\WinRAR\WinRAR.exe - full path to the WinRar program
с:\archive\arch.rar - path to the archive file
"c:\MyFiles\" - path to the folder prepared for archiving. You should pay attention to the fact that the paths to folders, where there is at least one Cyrillic character or a space in the name, must be enclosed in quotation marks.
Dear friends, it's no secret that Linux users are always turning their noses up at Windows users. They say that for Windows you need to install the application for at least 10 minutes, pressing a large number of buttons, tinkering with the checkboxes. And before you actually install the application, you need to find the official website of the program, while not getting lost on the Internet. Linux users are proud that they can install any utility from the terminal by running a specific command.
Windows has, like Linux, the ability to install, remove, or edit programs using commands.
The developers claim that Windows 10 will also have the ability to quick installation, updating and removing various software from the system terminal. It remains to wait for the official release. But you can not wait for the release, but right now take advantage of an amazing feature that will allow the user to install the program from the command line. However, this is not all surprises: the utility will also allow you to uninstall, update, open and close the program. Interesting? Let's get to know Chocolatey better.
Installing the program via the command line
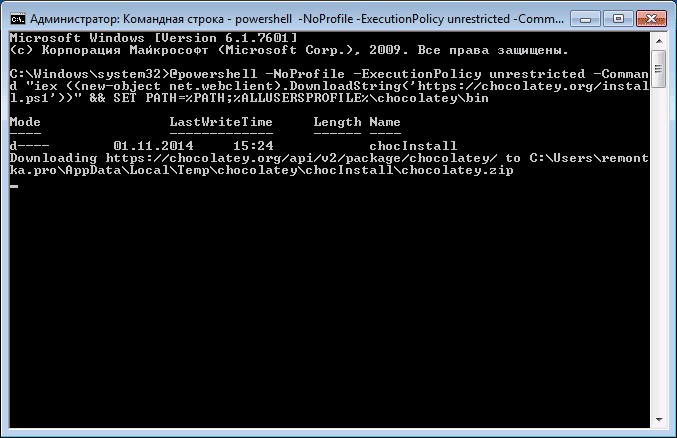
Now we will try to manage programs in a more convenient and very similar way to how it is done in a Linux environment. And the special service Chocolatey, a package manager for Windows, will help us with this. The Chocolatey client is a console-based utility. Let's try to install it right now. To install, open a terminal with administrator rights. Right-click on the Start menu and click Command Prompt (with administrator privileges). Now let's copy the following code:
@powershell -NoProfile -ExecutionPolicy unrestricted -Command "iex ((new-object net.webclient).DownloadString('https://chocolatey.org/install.ps1'))" && SET PATH=%PATH%;%ALLUSERSPROFILE% \chocolatey\bin
Paste and press the Enter key. Now you need to close the console so that the data on the variables is refreshed.
The Chocolatey service has a large catalog of utilities and applications: at the moment there are more than 2000 utilities. You can view them on the official website https://chocolatey.org/packages. So, it's time to learn how to install any program through the command line:
Open the terminal again as an administrator. We copy the text presented to the right of the program on the site https://chocolatey.org/packages. For example, to install a browser Google Chrome the following code is presented:
choco install googlechrome -y
Copy it and paste it into the terminal. Do not forget to write the -y combination after the code from the site. We press Enter. Now it remains to wait for the installation of the browser to complete. Then you can close the terminal window.
As could be seen, Google browser Chrome installed very quickly. We did not have to click any buttons, choose the location to save the files (the default is drive C). By the way, novice users can make a set of their favorite applications in a notebook so that they do not have to go to the Chocolatey service every time. To uninstall a program from the command line, type uninstall followed by the name of the program. For example, choco unistall ccleaner.
ATTENTION. The service works only with those packages that are installed through it. That is, if any software is not available for installation through Chocolatey, then you will not be able to remove it in this way.
How to run or uninstall a program through the command line
Now let's look at a way that allows through the command line. This can be done in three very simple steps. Let's get started:
- Opening the terminal operating system Windows.
- In the window that appears, write the full path to the location of the application launch file. For example D:/Files/chrome.exe
- We press Enter and wait until the system opens what we need.
It's time to learn how to close the program through the command line. To do this, we need additional taskkill software. Let's start.
This documentation has been archived and is no longer maintained.
Installing from the command line - specifying parameters
Applicable to: Forefront Protection for Exchange
Section modification date: 2010-05-10
The following table summarizes the options that can be used when running the extracted setup package (setup.exe) from the command line:
| Parameter | Description | Requirements |
|---|---|---|
| Silent installation - not displayed on the screen | Required parameter /a Optional parameter /c |
|
| Passive installation - no prompts to the user, but showing the progress | Required parameter /a Optional parameter /c |
|
| /aPathtoAnswerFile | Specifies a required response file | Answer file is required /q or /p |
| [/cPathtoConfigFile] | Specifies an optional configuration file | The config file is required Valid only with parameters /q or /p |
Before performing a passive or silent installation, you must extract the setup.exe file using the following command:
forefrontexchangesetup.exe /x: extractpath
Installation without user intervention allows during Microsoft installations Forefront Protection 2010 for Exchange Server (FPE) apply scripts. This type of installation does not display any notifications about the status of the installation. All output is written to the installation log, program log, or event log. Silent installation can be used to perform unattended and distributed installations on Exchange servers. Silent installation requires an answer file, which is provided using the option /a. A response file template that can be modified to suit your environment is provided in the installation package along with an XML Schema (.xsd) file that you can use to validate the resulting response file. If a valid response file is not provided, the installation is aborted and errors are logged. For information about viewing a sample response file, see .
After extracting the installation package ( additional information see section ), you can run a silent installation with an answer file by typing the following at the command prompt:
setup.exe /q /a PathtoAnswerFile
The answer file contains answers to all questions that you may have during the installation. This is a required parameter. In addition, you can specify the option /c
setup.exe /q /a PathtoAnswerFile/
A passive installation works in the same way as a silent installation, but it displays a progress bar that shows the progress of the installation.
After extracting the installation package (see the section for more information), you can run a passive installation with an answer file by typing the following at the command prompt:
setup.exe /p /a PathtoAnswerFile
The answer file contains answers to all questions that you may have during the installation. This is a required parameter. (For information about viewing a sample response file, see ). In addition, you can specify the option /c, which allows you to optionally import configuration settings to the server after installation is complete. These are settings that have been exported from another server. The syntax should be:
setup.exe /p /a PathtoAnswerFile/
Absolutely all programs can be run from the command line. This feature appeared in the first operating systems, including the line Microsoft systems Windows. Previously, operating rooms were a solid command line (MS-DOS system). Today, many software developers include in their distribution the ability to run as a single file using the command line.
You will need
- Operating system command line (cmd.exe).
Instruction
Click the "Start" menu - select "All Programs" - "Accessories" - "Command Prompt";
In the window that opens, you need to return to the "C" drive, for this, at the end of the line, enter "cd .." and press Enter. Repeat this action several times until the complete transition to the "C" drive;
Enter the full path to the program you are running (C:\Program Files\KeyTweak\KeyTweak.exe).
C:\Program Files\KeyTweak\KeyTweak.exe - full path to the Key Tweak program. The Key Tweak program parameters used in this example are:
- "u" - quick launch programs;
- "-r" - restore the last save changes;
- "-y" - answer "Yes" to requests coming from the system.
Create new Text Document with .txt extension.
Write down the required set of commands.
After completing these steps, run the file.
Rate this article!From the command line, you can start the installation of the program in interactive or silent mode.
Also, when installing the program from the command line, you can set up a username and password to access the program. The program will ask for a username and password when the user tries to uninstall or stop it, or change its settings.
To launch the application installation wizard from the command line,
enter setup.exe or msiexec /i at the command line<название дистрибутива> .
To install the application or update the application version in silent mode (without launching the application installation wizard),
enter setup.exe /pEULA=1 /pKSN=1|0 /pINSTALLLEVEL= at the command line<значение>/pALLOWREBOOT=1|0 /pSKIPPRODUCTCHECK=1|0 /pSKIPPRODUCTUNINSTALL=1|0 /s
msiexec /i<название установочного пакета>EULA=1 KSN=1|0 INSTALLLEVEL=<значение>ALLOWREBOOT=1|0 ADDLOCAL=<значение>SKIPPRODUCTCHECK=1|0 SKIPPRODUCTUNINSTALL=1|0 /qn ,
- EULA=1 means you accept the terms License Agreement. The text of the License Agreement is included in . Acceptance of the terms of the License Agreement is a prerequisite for installing the program or updating the version of the program. If the value of this parameter is not specified during installation in silent mode, the program will not be installed.
- KSN=1|0 means consent (1) or refusal (0) to participate in the Kaspersky Security Network program (hereinafter referred to as "KSN"). The text of the Statement of Participation in KSN is included in the distribution kit of Kaspersky Endpoint Security. Specifying a parameter value is optional. If the value of the KSN parameter is not specified in the command, then when you first start Kaspersky Endpoint Security a window with a request to participate in the KSN program will open.
- INSTALLLEVEL=<значение>indicates the installation type of Kaspersky Endpoint Security . Specifying a parameter value is optional. If the value of the INSTALLLEVEL parameter is not specified in the command, the standard installation of the program is performed by default.
Instead of<значение>you can specify the following values for the INSTALLLEVEL parameter:
- 100 . Performed basic installation programs.
- 200 . The standard installation of the program is in progress.
- 300 . All program components are being installed.
- ALLOWREBOOT=1|0 means consent (1) or prohibition (0) to automatically reboot the computer if it is required after installing or updating the application. Specifying a parameter value is optional. If the command does not specify the value of the ALLOWREBOOT parameter, by default, automatic restart of the computer after installing or updating the program is disabled.
It may be necessary to restart the computer after updating the version of the program or if during Kaspersky installations Endpoint Security detected and removed third party antivirus software.
- ADDLOCAL=<значение>specifies which components should be installed in addition to the components selected by default in the standard installation. Specifying a parameter value is optional.
Instead of<значение>you can specify the following values for the ADDLOCAL parameter:
- MSBitLockerFeature . The Microsoft BitLocker Manager component is being installed.
- AntiAPTFeature . The KATA Endpoint Sensor component is being installed.
- SKIPPRODUCTCHECK=1|0 means enable (1) or disable (0) check for incompatible software. Specifying a parameter value is optional. If the value of the SKIPPRODUCTCHECK parameter is not specified in the command, by default Kaspersky Endpoint Security performs a scan and displays a list of detected incompatible applications.
- SKIPPRODUCTUNINSTALL=1|0 means consent (1) or prohibition (0) to automatic removal of found applications that are incompatible with Kaspersky Endpoint Security. Specifying a parameter value is optional. If the value of the SKIPPRODUCTUNINSTALL parameter is not specified in the command, by default Kaspersky Endpoint Security tries to uninstall all found incompatible applications.
To install the application or update the version of the application with a username and password that confirm the right to change the application settings and operate the application, do the following:
- If you want to install the program or update the program version interactively, enter the following command at the command line:
setup.exe /pKLLOGIN=<Имя пользователя> <область действия пароля>
msiexec /i<название дистрибутива>KLLOGIN=<Имя пользователя>KLPASSWD=***** KLPASSWDAREA=<область действия пароля> .
- If you want to install the program or update the program version in silent mode, enter the following command at the command line:
setup.exe /pEULA=1 /pKSN=1|0 /pINSTALLLEVEL=<значение>/pKLLOGIN=<Имя пользователя>/pKLPASSWD=***** /pKLPASSWDAREA=<область действия пароля>/s
msiexec /i<название дистрибутива>EULA=1 KSN=1|0 INSTALLLEVEL=<значение>KLLOGIN=<Имя пользователя>KLPASSWD=***** KLPASSWDAREA=<область действия пароля>ALLOWREBOOT=1|0/qn .
Instead of<область действия пароля>you can specify one or more of the following values for the KLPASSWDAREA parameter (separated by a semicolon) corresponding to the operations that require confirmation:
- SET. Change program settings.
- EXIT. Completion of the program.
- DISPROTECT . Disabling protection components and stopping scan tasks.
- DISPOLICY . Shutdown Kaspersky policies security center.
- DISCTRL . Turn off control components.
- REMOVELIC. Removing a key.
- UNINST. Uninstalling, modifying or restoring a program.
- REPORTS. View reports.
During installation of the application or updating the application version in silent mode, the use of the following files is supported:
- setup.ini , which contains general settings for installing the program;
- the install.cfg configuration file containing the settings for Kaspersky Endpoint Security;
- setup.reg containing registry keys.
The setup.ini, install.cfg, and setup.reg files must be located in the same folder as the distribution package of Kaspersky Endpoint Security 10 Service Pack 2 for Windows.