Problems with the controller hard drives occur quite often. They may be the result of a PC power failure, overheating, moisture, or occur without visible reasons. A board defect may be visible (for example, when it is mechanical damage or burnout of elements) or invisible (the board is usually screwed in such a way that all its elements are hidden by the disk case).
Then carefully lift the hand holding each head to slide it back along the disc. At this point you should test your hand by swinging it back and forth very slowly and carefully. It shouldn't drag the disk at all. Insert the drive lock and head lock, and then the permanent magnet.
Reclose the case and turn on the controller again. Connect the drive and you should be good to go. This is a last resort for obtaining data and you should not rely on it. The heads appear to hang together, but much smaller. What. If the upper and lower heads are designed for one double-sided plate. touch, they are damaged to some extent.

Symptoms
Most often, there are no sounds, the engine does not rotate, the disk is not detected. The board elements may become excessively hot, and a short circuit on the disk board will not allow the computer itself to turn on. In unusual cases, the engine spins up, after which a rhythmic knocking sound is heard. This is a symptom of broken heads, and sometimes the result of their lack of correct control, for which the board element is responsible.
Heads play an amazing role in movement. As the plates rotate, the surface of the disk generates a small “film.” air that rotates in the same direction as the dish. When air passes under the head, the design of each head is such that it is very small. amount of air under the head and gently lifts the head from the surface. disk, so little that it does not move on the surface.
When you push the reinforcement along the surface of the disk, you. introduce small, perhaps microscopic scratches into the surface. dish. You also wear out a very small amount of the head's silicon. Now when you get to the edge of the plate, the two heads no longer work. separated by a dish, and plopped together ever so softly. In the microscopic world, a slap in the face is similar to that together with two skyscrapers. They may not be bursting into a million pieces, but infinitesimal chips and. cracks appear on the surface of the head.
Related Issues
Since the disk with the faulty board is “immobilized,” this problem is an obstacle to identifying many other diagnoses. The most common unpleasant addition is a malfunction of the magnetic head unit, since if there are power problems, the internal electronics may also suffer.
Cheating problems
A board malfunction can easily be confused with other problems. Without hearing the disk rotate, you can incorrectly diagnose a disk with a jammed motor. However, if you have already found out that the disk is faulty, it is important not to connect it to power, since in this case there is a high probability of failure of all the electronics of the disk, and at the same time the motor.
When you put the device together, you introduce stress and over time - maybe a week, maybe a year - the surfaces get scratched, worn out, and the head no longer flies. So how do you do this without destroying the drive? Build yourself a comb system that will spread the heads and lift them off the plate. before moving them at all. We use a series of metal fingers that taper to get under the rebar and lift the heads.
Automatic detection of hard drive type
Then pull out the fittings and comb assembly and remove, but if you pull the comb out. The point is that you can't see the damage done, it may not be catastrophic, but it will cause failure on an early drive. Perhaps you could put something together. perform the pendulum armature maneuver, but be careful.
And another interesting feature of the diagnosis
The diagnosis “Controller” can be made not because the board itself is faulty, but because to solve other disk problems, exactly the same manipulations are required as in case of its malfunction. For example, this applies. It's all about their “onboard”, that is, soldered onto the board itself, USB interface. It does not allow sending ATA commands to the drive and operating in special technological modes, and therefore we can use all the advantages of the PC3000Express hardware and software complex only by “bypassing” the USB interface, which is unsuitable for these purposes. Therefore, for external WD 2.5′ drives, any diagnoses of hardware faults are supplemented with a “controller” diagnosis, even if it is working.
Make sure it holds the heads together securely by rotating them. plates and keeps them out of the way while you make the switch. And never allow anyone to touch or slide on the surface of the plate! Also, all cleanliness is important. Not that you can't do it, just make sure there's no dust or small particles in the case. Imagine if one of your eyelashes hit the surface of the disc. If it appears when you spin the disc, you can wedge it under your head and perform it. almost the same as the head.
Burnout of HDD controller only
Remember that black powder? One of the most amazing parts is its mysterious module designed to reprogram or reprogram the firmware on a computer's hard drive using malicious code. The Kaspersky researchers who discovered this claim their ability to undermine the firmware hard drive- the guts of any computer - surpasses anything else they've ever seen.
The hard drive consists of two main parts: the HDA and the controller.
Figure 1 – block – hard drive diagram

Figure 2 – Basic design elements of a hard drive
1.2. Hard drive device
The entire hard drive, as a device, is divided, as we noted, into two large components: an electronics board and a hermetic zone or “can”, inside of which there are already magnetic disks, a block of magnetic heads, and a spindle motor.
It also has another capability: create invisible space on the hard drive to hide data stolen from the system so that attackers can recover it later. The flash module is most likely reserved for significant systems that present special surveillance challenges.
Mechanical damage to the hard drive controller
Costin Raiu, director of Kaspersky's Global Research and Analysis Group, believes these are high-value computers that are not connected to the Internet and are protected with disk encryption. Here's what we know about the firmware module. Trojanized firmware allows attackers to remain in the system even with the help of updates software. If a victim, thinking his computer is infected, wipes operating system computer and reinstalls it to eliminate any malicious code, malicious code The firmware remains intact.

 Figure 3- Appearance hard drive from MAXTOR
Figure 3- Appearance hard drive from MAXTOR
1.3. Electronics board (controller)
The electronics board or controller on the hard drive is essentially a small computer.
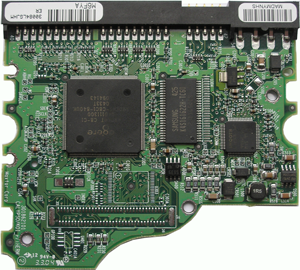 Figure 4 - External view of the electronics board (controller) of the MAXTOR hard drive
Figure 4 - External view of the electronics board (controller) of the MAXTOR hard drive
He can then contact the command server to restore all other malicious components that were removed from the system. Even if the firmware itself is updated from new version vendor, malicious software code may persist because some firmware updates only replace parts of the firmware, meaning the malicious parts cannot be overwritten by the update. The only solution for the victims is to destroy them HDD and start over again.
The attack works because the firmware was never designed with security in mind. Hard drive manufacturers do not cryptographically sign the firmware they install on the drives the way software vendors do. Additionally, hard drives do not have built-in authentication to verify signed firmware. This allows someone to change the firmware. an ideal place to hide malware, since antivirus scanners do not look at it. It is also not easy for users to read the firmware and manually check if it has changed.
On the board of modern hard drives you can find a processor, memory (RAM), and ROM. The processor processes the data received from the heads and converts them into a “language” understandable to the computer - the ATA standard. He does this, just like a computer in random access memory RAM. ROM is needed to start, like BIOS on motherboard. What the engine control chip does is clear from its name. When turned on, the controller board reads service information and if it is correct, the hard drive starts working. But what to do if the electronics board fails and, as a result, there is no access to documents, photographs, etc., because the hard drive is broken?
When is it necessary to replace the controller on a hard drive?
Do you know how much effort it takes to install just one firmware on a hard drive? Kaspersky researchers called it "an amazing technical achievement and a testament to the team's capabilities." They hide this data in what is called a hard drive's disk maintenance area, where the hard drive stores data necessary for its internal operation.
Hidden Vault - Holy Grail
The revelation that firmware tweaks help store data that attackers want to steal wasn't much of a play when the story broke last week, but it's the most significant part of the hack. This also raises a number of questions about how exactly attackers capture this. Without actual copy useful information firmware that gets into infected systems, there is still a lot unknown about the attack, but some of it can be guessed.
Of course, there is a desire to exchange this ill-fated board for a similar one from the “donor” hard drive, because they are so similar, and read your information. But not everything is as simple as it seems at first glance. As you know, progress does not stand still, and hard drive manufacturers are constantly improving their products, making changes to hard drive manufacturing technology and, as a result, new lines of hard drive models appear that differ in recording density, firmware, design of individual components, and electronics board circuitry. It is for this reason that on most hard drives the controllers have fine-tuning parameters and are not interchangeable.
This is especially useful if you have disk encryption enabled on your computer. However, there is a lot of space on the chip for a lot of data or documents, so attackers could also simply store something equally valuable to bypass the encryption. One of the five machines they found was trapped in a firmware flash module, had no Internet connection, and was used for ad hoc secure communications. So, if you want to get information from your computer, how do you get it?
You get the documents to a hidden area and you wait and then after one or two years you come back and steal it. They won't need a password if they can copy the entire directory from the operating system to a hidden sector for later access. But the flash chip that contains the firmware is too small for large amounts of data. Thus, attackers will need more hidden storage space. There are also large sectors in the disk maintenance area of a hard drive that are also unused and can be brought into use to store a large cache of documents, even those that may have been deleted from other parts of the computer. The area, also called the reserved or system area, stores the firmware and other data needed to control the drives, but also contains large portions of unused space.
Therefore, the conclusion: without complete information about the interchangeability of controllers on hard drives, unskilled independent attempts to recover data in the event of replacing the electronics board can not only aggravate the cause of the failure, but also significantly reduce the chances of successfully recovering information from the HDD.
Writing or copying data to a service area requires special commands that are specific to each vendor and are not published publicly, so an attacker would need to figure out what it is. It is also possible, although not trivial, to write a program to automatically copy documents into this area. However, one of the problems with hiding a large amount of data like this is that its presence can be detected by examining the amount of space used in the service area.
Footnote:
Hard drive controllers

Figure 5 - Controller
The drive controller itself is physically located on the electronics board and is designed to provide conversion operations and send information from the read/write heads to the drive interface. Often, a controller is called a drive interface or a PC interface with a drive, which is generally not true.
To do this, the implant prevents the system from revealing the true amount of free disk space. "The idea would be to change the firmware of a particular hard drive so that it typically recognizes, say, half of the available space," the document says. "It will report this size to the operating system and will not provide any access to additional space." The partition table will only show one partition of the disk, leaving the remaining partitions - where hidden data has been stored - invisible and inaccessible.
A hard drive controller is a complex device - a microcomputer, with its own processor, RAM and ROM, circuits and input/output system, etc. However, in most cases, manufacturers place them on one or two microchips.
The controller handles many data stream transformation operations. Since the lengths of the tracks are unequal, data must be written to different tracks unevenly. This becomes a problem, compared to floppy disks, for high-density media (more than 1000 tracks). Simple controllers typically write the same amount of information to each track, regardless of its length. To do this, the controller packs the data more densely, starting from a specific track. The cylinder (in the case of more than one disk, all the tracks below each other are called a cylinder) from which denser data packing begins is called the Starting Cylinder for Precompensation (SCP). To compensate for information distortion when reading, data is written with a preliminary bit offset, which takes into account the distortion.
The modified firmware will have a special hook built into it that will only unlock this hidden storage space after a custom command has been sent to the disk and the computer has been rebooted. Then hidden section will be available in the partition table and will be available until the secret storage is locked again using another user command.
Exactly how the spy agency planned to obtain the hidden data was unclear from the eight-year-old document. Document Type: Support Information. All elder users should think about where the journey will take them. The website offers informational transition materials for both private users and companies and institutions, without any real assistance.