FTP or File Transfer Protocol is a fairly ancient, but at the same time reliable and proven protocol for uploading files to a remote server or downloading them. Also, sometimes this protocol is used by webmasters to manage files or organize data storage.
In this article we will look at how to install FTP on Ubuntu 16.04, how to configure all the necessary components, including a secure connection. We will use the FTP server VSFTPD or Very Secure FTP Daemon, which provides the most reliable protection against vulnerabilities.
The program is available from official repositories, so installing FTP on Ubuntu Server 16.04 should not cause problems. First, update the list of packages in the repositories, then install the program itself:
sudo apt update
$ sudo apt install vsftpd
When the installation is complete, you need to enable the service vsftpd, since it will not be started by default, and also add the service to startup:
sudo systemctl start vsftpd
$ sudo systemctl enable vsftpd
If you have ufw firewall installed, and this situation occurs when you try to install FTP on Ubuntu Server, you need to open ports 20 and 21 for normal operation. To do this, run the commands:
sudo ufw allow 20/tcp
$ sudo ufw allow 21/tcp
$ sudo ufw status
The Ubuntu FTP installation is complete, but now you just need to configure everything you need to ensure a secure experience. Never use an FTP server with default settings on production networks, it is not secure.
Setting up FTP Ubuntu
Now let's move on to the setup. We only need to change a few parameters to fully secure your FTP server. First, we will look at the most obvious settings: disabling anonymous login and so on. First you need to copy the original settings file so that in case of problems you can return everything as it was:
sudo cp /etc/vsftpd.conf /etc/vsftpd.conf.orig
Then open the file in an editor:
sudo vi /etc/vsftpd.conf
Then add these settings. You will need to find and change the values of the specified strings; you should not add new ones if they already exist. First, disable anonymous login:
anonymous_enable = NO
We allow the use of local user names to log in:
write_enable = YES
Set the value umask for new files created via FTP:
local_umask = 022
We include a message about the need to select a directory after registration:
dirmessage_enable = YES
Record all file transfer transactions in a log file and use the standard log format:
xferlog_enable = YES
xferlog_std_format=YES
Use port 20 for data transmission instead of random, this is necessary for normal firewall operation:
connect_from_port_20 = YES
We indicate that we need to wait for incoming connections:
Use PAM service vsftpd:
pam_service_name=vsftpd
Finally, let's allow authentication of only the users listed in the file userlist:
userlist_enable = YES
We specify the file with our virtual users:
userlist_file=/etc/vsftpd.userlist
By default, such users are not allowed to log in, but we want the exact opposite, so add this line:
userlist_deny=NO
When users log into an FTP server, they can only work in the FTP root directory. If you want users to be limited only to their home folder, then you need to uncomment these lines:
chroot_local_user = YES
allow_writeable_chroot = YES
The first line indicates that the user should be placed in an isolated home directory, and the second that he can be allowed to write to this directory. Ubuntu FTP setup is almost complete, save the changes to the config file and restart vsftpd:
sudo systemctl restart vsftpd
Testing vsftpd
The server is ready, but the system is not yet fully configured. First let's create our test user using useradd:
sudo useradd -m -c "Test User" -s /bin/bash testuser
$ sudo passwd testuser
Since we want to connect to the FTP server on its behalf, we need to add it to vsftpd.userlist:
echo "tester" | sudo tee -a /etc/vsftpd.userlist
$ cat /etc/vsftpd.userlist

Now is the time to connect to our FTP server and check how everything works there. Let's try to log in as an anonymous user:

We won't succeed. Now let's try to log in as our test user, and everything will work as it should.
Note that it is dangerous to give users write access to their home folder. Do this only if you are sure that it is necessary and safe.
Setting up user home folders
To somehow get around the security issues, you can use a different folder instead of the home folder to provide it to the user. First, let's create a folder like this for our user:
sudo mkdir -p /home/testuser/ftp/files
Let's remove write permission for the ftp folder:
sudo chown nobody:nogroup /home/testuser/ftp
$ sudo chmod a-w /home/testuser/ftp
Then give the necessary permissions to the user to write to the subfolder.
sudo chown -R testuser:testuser /home/testuser/ftp/files
$ sudo chmod -R 0770 /home/testuser/ftp/files/

Now let's return to the vsftpd.conf configuration file. First comment out the line:
allow_writeable_chroot = YES
Now add these lines:
user_sub_token = $USER
local_root=/home/$USER/ftp
The first one adds a $USER variable that contains the username, and the second one sets the root folder for each user. All that remains is to restart the FTP server again:
sudo systemctl restart vsftpd
You can now log in as that user again and you will see that the folder we specified is now in use.

Setting up a secure connection
The installation of FTP on Ubuntu 16.04 is complete, but nowadays it is not safe to use open data transfer over the network. Everything possible should be encrypted. Therefore, we will look at how to set up a secure connection for vsftpd. First, let's create a folder and generate the certificate itself that we will use:
sudo mkdir /etc/ssl/private
$ sudo openssl req -x509 -nodes -days 720 -newkey rsa:2048 -keyout /etc/ssl/private/vsftpd.key -out /etc/ssl/private/vsftpd.pem

Then you need to allow access to the ports of the secure FTP connection with the UFW firewall:
sudo ufw allow 990/tcp
$ sudo ufw allow 40000:50000/tcp
$ sudo ufw status
All that remains is to make a few changes to the settings of the FTP server itself. We need to enable ssl_enable and disable encryption support sslv2 And sslv3, we leave only tlsv1:
ssl_enable=YES
ssl_tlsv1=YES
ssl_sslv2=NO
ssl_sslv3=NO
rsa_cert_file=/etc/ssl/private/vsftpd.pem
rsa_private_key_file=/etc/ssl/private/vsftpd.key
Prevent anonymous users from logging in via SSL:
allow_anon_ssl=NO
force_local_data_ssl=YES
force_local_logins_ssl=YES
Now let's install the most complex SSL cipher:
ssl_ciphers=HIGH
And configure the range of ports for data transfer:
pasv_min_port=40000
pasv_max_port=50000
It remains to restart our service:
sudo systemctl restart vsftpd
Now let's test what we got:


Now all data will be transmitted over an encrypted connection. The installation of Ubuntu FTP Server is complete.
conclusions
In this article, we looked at how to install FTP on Ubuntu Server 16.04, as well as how to configure FTP for maximum security, including setting it up over SSL. If you have any questions, ask in the comments!
In this article we will look at installing and configuring the vsftpd FTP server on a web server running the Ubuntu Server 18.04 operating system.
FTP (File Transfer Protocol) is a protocol for transferring files over a network. Default ports: 21/TCP for commands, 20/TCP for data. Ports for passive connection are configured additionally in the configuration file.
Installation
First, let's update the software package indexes:
sudo apt update
Now we install the FTP server itself:
sudo apt install vsftpd
Settings
Open the configuration file for editing:
sudo nano /etc/vsftpd.conf
Omitting comments, its content should be as follows:
listen=YES
local_enable=YES
chroot_local_user=YES
check_shell=NO
write_enable=YES
xferlog_enable=YES
chown_uploads=YES
chown_username=nobody
anonymous_enable=NO
pasv_enable=YES
pasv_min_port=60000
pasv_max_port=60100
Configuration file
Restart the FTP server:
sudo service vsftpd restart
Create an FTP user:
sudo adduser ftpuser
We create a directory to mount the site directory to our user’s home directory:
sudo mkdir /home/ftpuser/site
We mount:
sudo mount --bind /var/www /home/ftpuser/site

Mounting directories
Now /home/ftpuser/site will display files that are located in /var/www. Please note that the mount persists until the server is rebooted. After the reboot, the command will need to be repeated.
sudo chown www-data:ftpuser /var/www/ -R
sudo find /var/www -type d -exec chmod 775 () \;
sudo find /var/www -type f -exec chmod 664 () \;
In order for the user to connect via FTP, you need to enable a write ban in the root of the home directory:
sudo chmod a-w /home/ftpuser/
Now we need to configure the firewall for the connection:
sudo ufw allow in 20/tcp
sudo ufw allow in 21/tcp
sudo ufw allow in 60000:60100/tcp
Checking the rules:
sudo ufw status

Rule checking
All. Let's try to connect via FTP.

FTP connection
As you can see, the connection works. The mounted directory contains the files of our test site.
conclusions
The installation of the FTP server on the web server is completed. Now you can upload site files to the server and make backup copies. If you have any questions about this topic, write in the comments.
From time to time, every system administrator has a need for an FTP server, most often this is due to the need to ensure automatic exchange of information between applications, for example, during automatic exchange of a distributed 1C information base, or to access files on a web server. Today we will tell you how to create such a server on the Ubuntu platform in less than half an hour.
But first, a little theory. The FTP (File Transfer Protocol) protocol is intended, as the name suggests, for transferring files and appeared in 1971, but despite its advanced age it continues to be widely used to this day. Although its use today is more technical in nature, end users typically use a browser and the HTTP protocol to access data. The advantages of FTP include the ability to resume downloading a file when the connection is lost and the ability to equally easily read files and write them. But there are also disadvantages, the most serious one being low security, so this issue should be given the closest attention.
FTP, like PPTP, uses different connections to send commands and transfer data. When initiating a connection, the client sends control commands to port 21 of the server, which in turn establishes an outgoing connection for data transfer on port 20, the port on the client side is determined as a result of negotiation. However, if the client is behind NAT, the connection cannot be established in this way, so an additional FTP passive mode was developed, when the connection for data transfer is established not by the server, but by the client, but with the parameters specified by the server. These points should be taken into account when forwarding FTP and when setting up a network filter.
For our server we will use vsftpd- simple, fast and secure FTP server. Since it will serve both external and internal networks, it makes sense to add this role to our . Server installation is extremely simple:
Apt-get install vsftpd
The server is configured through a configuration file /etc/vsftpd.conf it has a simple structure, is well commented and allows you to set up a server without any instructions with minimal knowledge. Let's consider its main parameters.
The server can be launched constantly, as a service, or started when necessary; the first option is more suitable for us:
Listen=YES
This option has a mutually exclusive entry, which should be given the following form:
Listen_ipv6=NO
Let's allow only local users to log in:
Anonymous_enable=NO
local_enable=YES
Let's allow users to write files and instruct the server to automatically set the necessary rights (755 for folders and 644 for files):
Write_enable=YES
local_umask=022
If you need to set a different set of rights: 775 and 664, then umask should be equal to 002.
By default, the server uses GMT time, so that files are set to your time zone, use the option:
Use_localtime=YES
Let's enable the log of uploaded and downloaded files:
Xferlog_enable=YES
Let's allow the server to establish connections to transmit data on port 20 (active mode):
Connect_from_port_20=YES
The following options specify the location and format for storing logs:
Xferlog_file=/var/log/vsftpd.log
xferlog_std_format=YES
Let's set session timeouts:
Idle_session_timeout=600
data_connection_timeout=120
Also, for security purposes, we isolate the user in his home directory and immediately allow writing to his root:
Chroot_local_user=YES
allow_writeable_chroot=YES
To work correctly with text data, you can enable ASCII support; this will allow, when transferring a text file from a Windows system to UNIX (Linux), to correctly replace line breaks from CR+LF to LF to correctly display the content and perform the reverse conversion when transferring it back.
Ascii_upload_enable=YES
ascii_download_enable=YES
You can only enable one option, for uploading or downloading. Please note that when transferring a binary file in ASCII mode, the latter may be damaged.
Quite an interesting option:
Ls_recurse_enable=YES
It allows recursive browsing of directories, on the one hand it is convenient, on the other hand it can cause a large load on the server if, for example, you get a listing of a directory containing a large number of files and directories.
We leave all other options as default, although you can edit the server greeting by writing whatever you like:
Ftpd_banner=Welcome to Roga i Kopyta LLC FTP
At the end of the configuration file, we will set the settings for passive mode; it is recommended to explicitly set the ports so that you can specify them during forwarding if the server is behind NAT or in firewall rules:
Pasv_enable=YES
pasv_min_port=62000
pasv_max_port=62999
Restart the server (this must be done every time after making changes to the configuration):
Service vsftpd restart
and try to connect with any FTP client using the credentials of an existing user. We must get into his home directory and be isolated in it.
If an error occurs due to incorrect operation of vsftpd and the seccomp security system:
500 OOPS: prctl PR_SET_SECCOMP failed
add an undocumented option to the file:
Seccomp_sandbox=NO
However, remember that FTP is an insecure protocol, so allowing any local user to the server, as is done now, is not the best option. To avoid this situation, vsftpd has a built-in user control mechanism. Let's add the option to the configuration file:
Userlist_enable=YES
and create a user list file:
Touch /etc/vsftpd.user_list
Default vsftpd prohibits access to the server for users specified in this list even before entering a password, i.e. implements the principle of allowing everyone who is not prohibited. But it would be much better to implement a different approach: everyone who is not allowed is prohibited. Those. allow access only to specified users. To do this, add an option:
Userlist_deny=NO
Now only explicitly specified users will have access to the FTP server; they should be specified in vsftpd.user_list one per line, for example:
Ivanov
petrov
Unless otherwise specified, when connecting via FTP, users are taken to their home directory. This is not always convenient; you often need to redirect them to another directory. If this is a common folder for everyone, say /var/ftp, then you can set the option:
Local_root=/var/ftp
Which will redirect all users to the specified directory and isolate them there.
This is the simplest situation, real tasks are usually more complicated, let’s say we need to set the user Ivanova as the root directory /var/www/example1.com, and Petrov /var/www/example2.com so that each of them works with their own folder. For these purposes, you can use another feature of vsftpd - user settings that override the settings of the main configuration file.
To do this, add an option:
User_config_dir=/etc/vsftpd_user_conf
Then we will create the directory itself
Mkdir /etc/vsftpd_user_conf
To set the user’s own settings in this directory, you should create a file with the user’s name and add the necessary options to it. The changes are applied without restarting the FTP server the next time the client connects.
Let's create a file with settings for Ivanov:
Tocuh /etc/vsftpd_user_conf/ivanov
and add an option to it:
Local_root=/var/www/example1.com
The next time you connect, the user's root directory will change to the specified one. Also in this file we can set any personal options, for example, other umask or file permissions. However, we cannot use global settings here: connection, logging, authentication options, they will simply be ignored.
If you need to hide the real owners of files and folders, you can use the option:
Hide_ids=YES
In this case, instead of real owners and groups, ftp:ftp will be indicated, this can be useful in the case of a public server or if there are strangers in the user list to whom you do not want to reveal the real user names of your system.
As you can see, we actually created a working FTP server in less than half an hour.
File Transfer Protocol (FTP) is a TCP protocol for transferring files between computers. In the past, it was also used to download [files on the Internet], but since this method does not use encryption, user data as well as the contents of files are transmitted in the open and are easily intercepted. So if you are here looking for a way to transfer and download files securely, better refer to the OpenSSH article in the Remote Administration section.
FTP operates on a client/server model. The server component is called the FTP service. It constantly listens for FTP requests from remote clients. When a request is received, it controls the login and connection establishment. During the session, it executes any commands sent by the FTP client.
vsftpd - installing an FTP server
vsftpd is an FTP service available on Ubuntu. It is easy to install, configure and maintain. To install vsftpd you can run the following command:
Sudo apt install vsftpd
To start the service you need to add it to startup. Starting from Ubuntu 15.04, Systemd is used, so to add vsftpd to startup you need to enter the following commands:
Sudo systemctl start vsftpd sudo systemctl enable vsftpd
Ubuntu Server may use the ufw firewall. Then you will need to allow ports 20 and 21
Sudo ufw allow 20/tcp sudo ufw allow 21/tcp
The configuration file contains many settings options. Information for each parameter is available in the same file. Alternatively you can look at the system manual for the command
Man 5 vsftpd.conf
to clarify details for each parameter.
Access to the FTP server can be organized in two ways:
IN anonymous mode The remote client can access the FTP server by using the default user account named "anonymous" or "ftp" and passing the email address as the password. IN authorized mode the user must have an account name and password. This last option is extremely unsafe and should not be used except in special circumstances. If you want to transfer files securely, see SFTP in the OpenSSH server section. User access to directories and files of the FTP server depends on the access rights of the user specified at login. Typically, the FTP service hides the root directory of the FTP server, replacing it with the FTP home directory. This hides the filesystem root from remote sessions.
Setting up anonymous access via FTP
The default setting of vsftpd does not allow anonymous booting. If you want to allow anonymous loading, change /etc/vsftpd.conf to the following:
Anonymous_enable=YES
The installation process creates a user ftp with home directory /srv/ftp. This is the default directory for FTP.
If you wish to change its location to, for example, /srv/files/ftp, simply create a new directory and change the ftp user's home directory:
Sudo mkdir /srv/files/ftp sudo usermod -d /srv/files/ftp ftp
After the changes, restart vsftpd:
Finally, copy all the files and directories you want to make available for anonymous FTP to /srv/files/ftp (or /srv/ftp if you want to leave the default settings).
By default, an anonymous user is not able to upload files to the FTP server. To change this setting, uncomment the following line and restart vsftpd:
Anon_upload_enable=YES
Allowing an anonymous user to upload files can be a serious security risk. It is better not to allow anonymous file uploads to servers with direct access from the Internet.
Setting up authorized access via FTP
Before making any changes to the configuration file, it is recommended to copy the sample so that you can roll back the changes without reinstalling the package sudo cp /etc/vsftpd.conf /etc/vsftpd.conf.orig
To authenticate local users, you need to uncomment the line
Local_enable=YES
By default, vsftpd is configured to authenticate system users with the ability to retrieve files. If you want to allow users to upload files, change /etc/vsftpd.conf:
Write_enable=YES
then restart vsftpd:
Sudo service vsftpd restart
Now when system users log in via FTP, they will be taken to their home directories where they can download, upload [files], create directories, etc.
FTP protection
User Restriction
There are options in /etc/vsftpd.conf to help make vsftpd more secure. For example, this option allows you to place a local user in a chroot() “imprisonment”, above which (in the directory tree) he cannot rise.
Chroot_local_user=YES
You can also define a list of users who only have access to the home directory:
Chroot_list_enable=YES chroot_list_file=/etc/vsftpd.chroot_list
After uncommenting these options, create /etc/vsftpd.chroot_list containing a list of users, one per line. Then restart vsftpd:
Sudo service vsftpd restart
If you uncommented all three lines, then users on the list will not be limited to their home directories, unlike users not included in the list
Similarly, the /etc/ftpusers file contains a list of users who are denied FTP access. By default it includes root, daemon, nobody, etc. To deny FTP access to additional users, simply add them to this list.
If you see an error when trying to connect:
Answer: 500 OOPS: vsftpd: refusing to run with writable root inside chroot()
then this means that the local user has write access to the home directory, which should not be the case. There are several ways to solve this error:
Deny writing to the home directory for a local user (not suitable for everyone and not always)
Set /home as the directory where local users will go after logging into the FTP server. Then each of them will be able to write only to their home directory
Encryption
FTP may be encrypted when used FTPS. Unlike SFTP, FTPS is FTP over SSL. SFTP is an FTP-like session over an encrypted SSH connection. The main difference is that SFTP users must have a shell account instead of a nologin shell. Giving all users shell access may not be the best solution for some systems, such as a public web server. However, there is an option to limit such accounts to SFTP only and prevent shell interaction. See the section on OpenSSH for more information.
To configure FTPS, add the following to the end of the /etc/vsftpd.conf file:
Ssl_enable=Yes
Also note the certificate and key options:
Rsa_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem rsa_private_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
By default these options are set to the values provided by the package ssl-cert. For a production environment, they should be replaced with a certificate and key created for a specific computer. For more information, see the Certificates section.
Now restart vsftpd and non-anonymous users will use FTPS:
Sudo service restart vsftpd
To allow users with the /usr/sbin/nologin shell to access FTP but not grant shell access, edit /etc/shells to add nologin to the shell:
# /etc/shells: valid login shells /bin/csh /bin/sh /usr/bin/es /usr/bin/ksh /bin/ksh /usr/bin/rc /usr/bin/tcsh /bin/tcsh / usr/bin/esh /bin/dash /bin/bash /bin/rbash /usr/bin/screen /usr/sbin/nologin
This is necessary because vsftpd uses PAM authorization by default, and the settings file /etc/pam.d/vsftpd contains:
Auth required pam_shells.so
PAM module shells restricts access to the shells listed in the /etc/shells file.
Most popular FTP clients can be configured to use FTPS. The lftp command line FTP client also has the ability to use FTPS.
It's time to organize file storage, both inside the network and outside. This article is a continuation of the first part, dedicated to setting up a WiFi router on your home server. All hard drives from your home computer (except the system one) can be transferred to the server, since the transfer speed fluctuates around 10-20 megabytes per second [this parameter also very much depends on the model of your hard drive], and by the way, for a long time now It's time to buy SSD drives for the system disk.
FTP Server.
There are many ftp servers for Linux, many good, many bad, but there is the best [of course, this is a subjective opinion, and the best one for me] and this is vsftpd. This is what we will consider.
You can download it from standard repositories OpenSUSE by running the command in the terminal:
zipper in vsftpd
Now let's move on to the description. This is a console ftp server, it does not have a GUI [graphical shell], so all configuration takes place in one single config, at /etc/vsftpd.conf.
Here is an example of a working config:
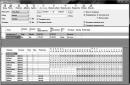
#allow any form of writing to the FTP server write_enable=YES #allow the ability to display messages about transitions from folder to #folder. dirmessage_enable=YES #select a user WITHOUT any privileges (read-only) nopriv_user=ftpsecure #allow local users (local users are those #registered in the system, that is, they have accounts) local_enable=YES #push the local user into chroot. chroot_local_user=YES #prohibit anonymous login to the server anonymous_enable=NO #enable logging syslog_enable=YES #allow to join on port 20 connect_from_port_20=YES #allow to upload folders with the Cyrillic alphabet ascii_upload_enable=YES #allow to download folders with the Cyrillic alphabet ascii_download_enable=YES # name of the PAM service in the system pam_service_name=vsftpd #ability to work in offline mode listen=YES #disable SSL authentication ssl_enable=NO #range of ports for PASV mode. pasv_min_port=30000 pasv_max_port=30100 #welcome when entering ftp-server ftpd_banner=Welcome to my ftp-server #time after how long a user will be kicked from the server if he is inactive idle_session_timeout=900 #maximum number of users max_clients=10 #maximum number of sessions from one ip addresses max_per_ip=3 #enable PASV mode (passive mode) pasv_enable=YES #mask of allowing privileges for local users. local_umask=0002
In the above config there are no problems for distributing access rights to individual users or individual folders. Everything is quite simple and concise, set it up once and use [use]. Vsftpd was chosen because it has the best system for setting up access rights, which is divided into two types: internal, system authentication and external, with a separate configuration file for assigning access rights, but at the same time, users are still taken from the system.
In this example, both users and the distribution of access rights for these same users are taken from the system; an additional config file is not used.
Figure 1. Setting rights
That's all.
Samba.
Do you want to always have file storage of all collections and everything else at hand from your laptop, home computer, phone, tablet? Go.
Initially, with a standard installation of the OpenSUSE system, everything that is needed to install and configure samba on the server is already preinstalled. Therefore, let's move directly to the setup. Since access from under Windows OS as “Map a network drive” will be available only within your local network [there is an ftp server for the Internet, and besides, posting samba on the Internet is extremely unsafe, but we, “FOR SECURITY! !! HURRAY!”] so the settings will be extremely banal and easy to understand. There are two [known to me and adequate in my opinion] samba settings, this is through the same configuration file and using the utility - WebMin. This is a wildly cool thing, especially for those who don’t like tinkering with configs [but there are some nuances here too]. In this article we will not dwell on the means " for the lazy", so we continue. We will look at the working config file. It is located at: /etc/samba/smb.conf. Here he is:
# Specify the name of the guest user. guest account = nobody # Specify the name netbios name = homeserver # Enable the "write" permission writeable = yes # Additional option that removes the delay. socket options = TCP_NODELAY IPTOS_LOWDELAY # If necessary, specify the workgroup where the computers will be located # (absolutely optional parameter) workgroup = HOMENET # Select the interfaces on which samba will “listen”. # (also an optional option, by default, all interfaces will be listened to) interfaces = eth1 wlan0 # Security is not particularly needed at home. security = share public = yes # Allow guest guest ok = yes # Guest only? Yes. guest only = yes # Path to the public folder path = /cifs/pub # Do not disable writing. read only = no # Also, if you are interested in the ability to access the CD-ROM, then insert # the following options into the samba config: fake oplocks = yes guest ok = yes guest only = yes path = /mnt/cdrom read only = yes
Also, additional configuration can be done through the samba GUI built into YaST.
The user that we specified at the very beginning of the config, in this example it is the user nobody, must be created directly in the system. Give it the necessary rights (at home, it makes sense to set full rights to create, delete, edit all files and folders (i.e. rights 777). Also, if you encounter a situation where for some reason it becomes impossible to delete/ creating files in any of the folders on the server, then run the command:
chmod 777 -R /path
Let's look at it, just in case:
chmod- command to set rights.
777
- the rights themselves, in the letter designation they mean rwx, rwx, rwx - read, write, execute rights for the owner, group (where the owner is a member), everyone.
-R- recursion key, so that the command is executed not only for the folder (and the files located in it) that you specified in /path, but also for all subfolders and files in them too.
/path- path to the folder for which you want to set rights. A similar command corresponds to the FTP server if similar problems occur. Yes, and we must make a reservation that if such problems arise, then most likely the problem lies in the users created in the system, or rather in the rights granted to use their home directories.
rTorrent.
Semi-automated torrent client.
In fact, this is an ordinary torrent client, but its customization options are very rich in variety. Now we will analyze one very useful function of this client. Imagine, you have already configured Samba on your home server, the file storage located on the server is connected to your computer as a Network Drive, you open your network drive, open the torrents folder, open the music folder there and move there all the torrent files with music that you you want to download and... that's it, go to bed. In the morning, the hashes of all the torrents that you put there will be downloaded and checked (here, of course, it all depends on how many torrents you want to download, what their weight is and what the width of your Internet channel is). Like? So I’ve been enjoying this function for about half a year now.
Let's figure it out.
You need to install rtorrent, run the following command in the terminal:
zipper in rtorrent
After you have downloaded and installed the rtorrent torrent client, you need to configure the client. The program is configured using a configuration file .rtorrent.rc, placed in the user's home directory. (By default, the .rtorrent.rc file is missing. You need to create it yourself. Here is an example with detailed comments on the working config:
#peer exchange? Yes! peer_exchange = yes #minimum number of peers per torrent min_peers = 1 #maximum number of peers per torrent max_peers = 1000 #maximum download speed download_rate = 0 #maximum upload speed. 1 - unlimited upload_rate = 0 #directory for saving downloads or from where torrents will be seeded. directory = /files/torrents #directory where the state of torrents will be saved. #Here, in this example, they are saved in the session folder session = /files/torrents/session/ #rtorrent checks this directory every 5 seconds for new *.torrent #files #and if there are any, it puts them on download #schedule = watch_directory ,5,5,load_start=/home/user/torrent_auto_load/ #checks directories for new *.torrent files and saves downloads to the #appropriate folders schedule = watch_directory,5,5,"load_start=/files/torrents/music/*. torrent,d.set_directory=/files/music" schedule = watch_directory_2,5,5,"load_start=/files/torrents/video/*.torrent,d.set_directory=/files/video" schedule = watch_directory_3,5,5, "load_start=/files/torrents/video/serial/*.torrent,d.set_directory=/files/video/serial" schedule = watch_directory_4,5,5,"load_start=/files/torrents/progs/*.torrent,d .set_directory=/files/progs" schedule = watch_directory_5,5,5,"load_start=/files/torrents/games/*.torrent,d.set_directory=/files/games" schedule = watch_directory_6,5,5,"load_start= /files/torrents/unsorted/*.torrent,d.set_directory=/files/unsorted" schedule = watch_directory_7,5,5,"load_start=/files/torrents/doc/*.torrent,d.set_directory=/files/doc "schedule = watch_directory_8,5,5,"load_start=/files/torrents/doc/books/*.torrent,d.set_directory=/files/doc/books" #Deleting torrent files from the music directory (because in this # For example, the music folder goes as "directory"(#1), which has already been downloaded. schedule = untied_directory,7,5,remove_untied= #number of the port (or several ports) that the client opens for #data exchange port_range = 40890-40890 #random selection of port for data exchange. In this case, it is #disabled port_random = no #check the torrent hash after downloading check_hash = yes #save the session session_save = yes #accept encrypted incoming connections, establish #unencrypted outgoing connections, #if it returns an error, repeat with encryption, prefer #plaintext after establishing #encrypted connection encryption = allow_incoming,enable_retry,prefer_plaintext #use udp use_udp_trackers = yes

Figure 2. Main window of the rTorrent program
That's all. Next is a tricky trick - open the console and write (you can also log into the server via ssh):
screen rtorrent
Next, the torrent client will open in the terminal, where you can further configure and debug it. Now press the magic key combinations Ctrl+A then Ctrl+D and the console will happily notify you that:

Figure 3. “Screening” of the rTorrent program process.
This indicates that the process of your torrent client is “zakrinin”, that is, it is running, but it is not visible. For those adherents who are always interested in everything, you can read here about this utility; I don’t want to burden my head with such things (although they are very interesting and educational, and are used often).
If you need to open the client again, write:
screen -r
IMPORTANT: If you want to run the torrent client under root (root, i.e. through the sudo command), then you need to create a config file in the root directory of the root user, and also, screen -r must also be executed under the same user as you she was “screened”.
Thus, you will always have a torrent client hanging in the background, which will download and distribute exactly as much as your server is running.
On this “important” note, I want to end this article. Thanks for your attention, and yes, use the search engine Google, he's great!
If I made the wrong topic, tell me where to move it.